Kong

Kong is an Open-Source API management solution provides by Mashape. In fact Kong "only" provides the first feature of an API management solution: The API gateway. Mashape also provides solutions for analytic and dev portal but not Open-Source. Respectively Galileo and Gelato. Nevertheless it's quite simple to link Kong with other great Open-Source solutions to cover other features.
Features
So Kong is "only" an API Gateway but with a lot of features. Kong have a pluggable architecture and all the features are provided through plugins.
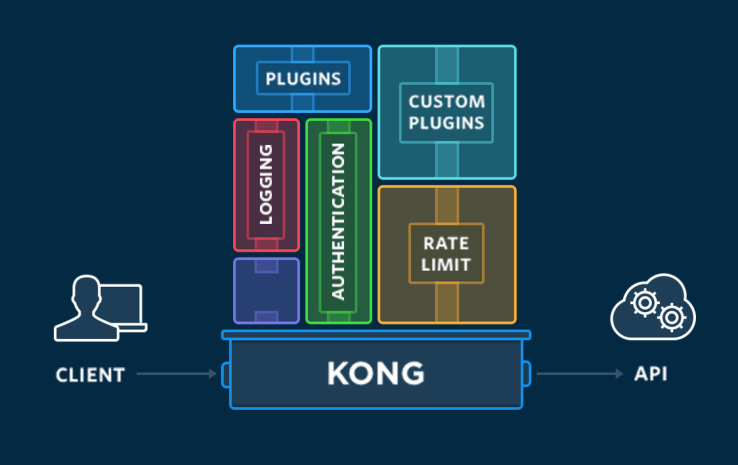
Current plugins are:
- Authentication: Protect services with an authentication layer
- Basic: Add Basic Authentication to your APIs, with username and password protection
- Key: Add Key Authentication (also referred to as an API key) to your APIs.
- OAuth2: Add an OAuth 2.0 authentication layer with the Authorization Code Grant, Client Credentials, Implicit Grant or Resource Owner Password Credentials Grant flow.
- JWT: Verify requests containing HS256 or RS256 signed JSON Web Tokens
- HMAC: Add HMAC Signature Authentication to your APIs to establish the identity of the consumer.
- LDAP: Add LDAP Bind Authentication to your APIs, with username and password protection.
- Security: Protect services with additional security layers
- ACL: Restrict access to an API by whitelisting or blacklisting consumers using arbitrary ACL group names.
- CORS: Add Cross-origin resource sharing (CORS) to your API.
- IP restriction: Restrict access to an API by either whitelisting or blacklisting IP addresses.
- Bot detection: Detects and blocks bots or custom clients.
- SSL: Add an SSL certificate for an underlying service.
- Traffic Control: Manage, throttle and restrict inbound and outbound API traffic
- Rate limiting: Rate-limit how many HTTP requests a developer can make.
- Response rate limiting: Rate-Limiting based on a custom response header value
- Request size limiting: Block requests with bodies greater than a specific size
- Analytics & Monitoring: Visualize, inspect and monitor APIs and microservices traffic
- Datadog, Galileo, Runscope: Send metrics to external analytic platforms.
- Transformation: Transform request and responses on the fly
- Request transformation: Modify the request before hitting the upstream server
- Response transformer: Modify the upstream response before returning it to the client
- Correlation ID: Correlate requests and responses using a unique ID
- Logging: Log requests and response data using several transport solution:
- TCP, UDP, HTTP, File, Syslog, StatsD, Loggly (a logging SaaS)
The feature catalog is very good. In the case of a missing feature you are able to develop your own plugin (as soon as you are comfortable with LUA).
Installation
A very simple way to setup Kong is Docker. Mashape provides an official image and source repository with a full setup that you can orchestrate with Docker Compose:
$ git clone https://github.com/Mashape/docker-kong.git
$ cd docker-kong
$ docker-compose up
This will setup:
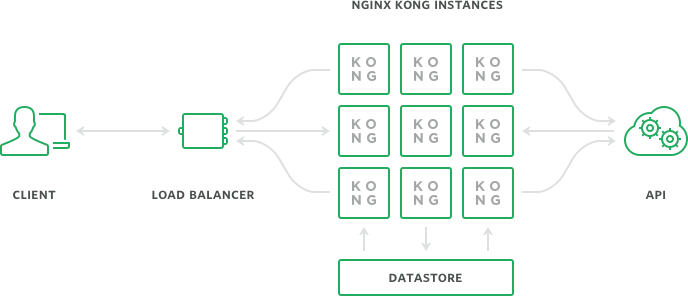
- A Consul instance to provide a service discovery registry.
- A NGINX load balancer that will use Consul (with Consul template) to discover Kong instances and balance the requests..
- A PostgreSQL database used by Kong as its data-store.
- And Kong instance.
If you are using a Docker cluster, you can scale up and down the number on instances using compose. It's also possible to do a manual setup if you want for instance use Cassandra.
Once the containers are started, you can access to the following exposed ports:
- 8000: API entry point of the Gateway.
- 8443: API SSL entry point of the Gateway.
- 8001: Configuration API of the Gateway.
- 8500: Consul Web UI.
Configuration
Kong is configured with an API. For now there is no official GUI or CLI. There exists some Open Source contributions. Some are quite mature but the most reliable tool you should use is cURL or HTTPie.
Example:
$ # Create an API
$ curl -i -X POST \
--url http://localhost:8001/apis/ \
--data 'name=mockbin' \
--data 'upstream_url=http://mockbin.com/' \
--data 'request_host=mockbin.com'
$ # Forward your requests through Kong
$ curl -i -X GET \
--url http://localhost:8000/ \
--header 'Host: mockbin.com'
Under the hood
Kong can be saw as a robust and mature solution simply because it's the engine of the Mashape catalog: about 15.000 API, billion of requests, 200.000 users.
Kong is built on top of NGINX HTTP server. NGINX is the reverse proxy processing the client requests to the upstream services. The preocessing is done thanks to LUA. A a powerful, efficient, lightweight, embeddable scripting language. Kong stores its configuration in a distributed datastore. This datastore can be powered with PostgreSQL or Cassandra (a great option for horizontal scale).
What next ?
So, Kong is a great base for an API management solution. BUT!
Even existing, some features are not complete. This is especially true for authentication plugins. They are covering the basic needs, but in a corporate context, authentication can be a bigger deal. The usual way is to use a an Identity and Access Management solution (IAM). This is a good transition to Keycloak.